SECURE IOT PLATFORMS
Protect your mission-critical, cellular IoT systems from cyber attacks.

This is part of the enterprise attack surface that no one has addressed. Until now, traditional IT security tools are not sufficient because they can’t see or control the Internet activity of cellular connected IoT devices. Your devices could connect to malicious actors on the Internet and you would never know it or be able to stop it.
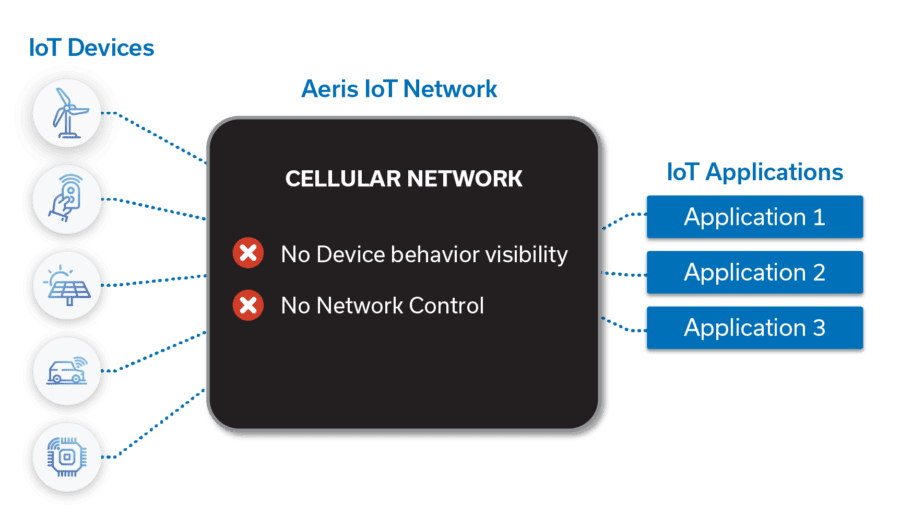

A cyber attack on your mission-critical IoT devices could result in downtime, loss of customers, potentially even loss of life.
Security controls are also needed to help your business comply with industry and government regulations.
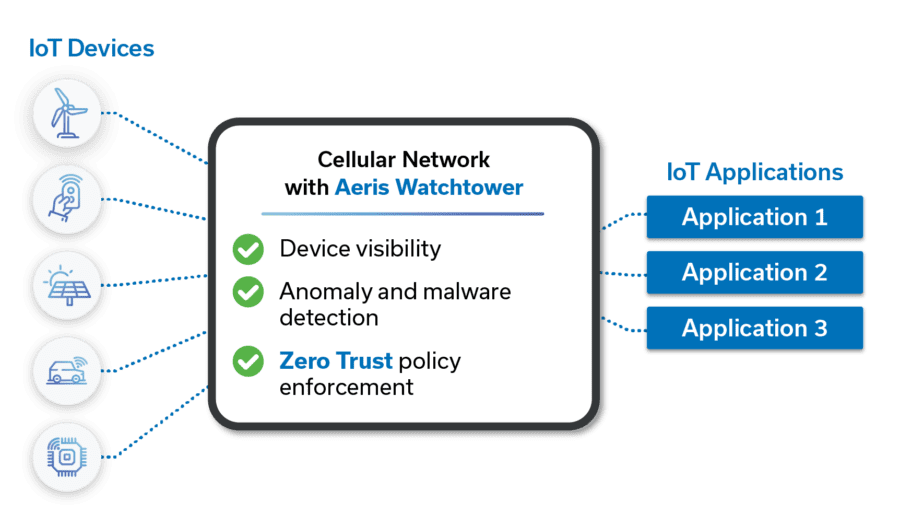
Aeris IoT Watchtower protects your enterprise from cyber attacks targeting your IoT devices. Aeris IoT Watchtower combines Zero Trust security principles of least privileged access with state-of-the-art malware and anomaly detection.
Aeris IoT Watchtower is simple to deploy because it is built into the Aeris cellular network. It requires no agents or software changes to your IoT devices. Just turn it on.
Keep learning. Keep evolving. Keep moving forward.
You no longer need to compromise on security. With Aeris, you get the best of both worlds: great connectivity paired with best-in-class security.
