This is especially true for organizations that use IoT to improve their business and better serve their customers. Recent statistics highlight the growing risk to IoT programs, identifying the need to take IoT security seriously.
- IBM identified that it takes more than 9 months on average to detect and contain cybersecurity breaches.
- Medigate and CrowdStrike discovered that over 80% of healthcare organizations reported facing IoT security incidents in the past 18 months.
- Kaspersky reported that 53% of organizations abandoned new business projects due to an inability to address cybersecurity risks.
The price of ignoring these risks for any organization is simply too high. It could cost your business millions of dollars, your customers significant hardships, and even damage your company’s reputation. In the case of healthcare, the stake is even higher. If there’s a breach of connected devices that monitor patients’ vital signs or determine when treatment is essential, the potential loss of human lives could lead to a costly class-action lawsuit.
Clearly, IoT security is not something to take lightly. With the demand for connected devices on the rise, having strong IoT network security provides an added layer of protection and reinforces your company’s security strategy.
IoT Network Growth
According to IoT Analytics, the total number of connected IoT devices is estimated to grow from 12.3 billion today to 27 billion by 2025, with the heaviest growth anticipated to come from the healthcare, manufacturing, transportation, energy, and utilities industries. This rapid expansion of IoT devices places added demand for strong security at all levels — data, device, application, and network — as well as a need for reliable, optimized performance.
As IoT programs scale up, the vast amount of data generated by devices becomes unmanageable for human beings to process and analyze manually. Without the ability to synthesize and act on this information, the benefits of these programs cannot be fully realized and the likelihood of security breaches going undetected increases.
IoT programs stand to benefit the most by adopting an intelligent network paired with advanced analytics to process data at record speeds, deliver results, and take action – on time. An advanced network intelligence approach, such as the one employed by Aeris, incorporates traditional data analytics techniques as well as machine learning (ML) and/or artificial intelligence (AI) that can help you prevent, detect, and respond to anomalies and potential threats.
IoT Security Challenges
Being able to identify a security breach and then mitigate it with prompt action can prevent costly security breaches. The challenge comes down to the issue of scale. When you have one device, it’s easier to manage. When you have hundreds or thousands of connected devices that could get breached in the same identical way, the issue of scale is significant. The sheer volume of devices leads to a greater attack surface. It also makes spotting a security breach across thousands of devices like trying to find the proverbial needle-in-a-haystack.
The central challenge lies in being able to identify the subtleties of the security breaches that were attempted and then take prompt action to mitigate them. To do both, you need visibility into device behavior and network activity. What makes this possible is deploying and scaling IoT programs on an intelligent network that harness the power of ML and AI.
For IoT devices that rely on cellular connectivity for broad geographical coverage, there is an added complexity when it comes to cybersecurity. Strong end-to-end security can be difficult if the control and data packets traverse from one carrier’s network to another.
Having an up-to-date and effective security posture is challenging but essential. Recognizing a problem exists is the first step before taking appropriate action. You would need to know specifically what’s happening, in which location, and on which devices. The sheer volume of devices makes detection difficult. In addition, corrective action would need to be applied to thousands of potentially vulnerable devices. The final step would be to analyze and learn from the security breach so that future attempts can be thwarted.
If you happen to be thinking, as you’re reading through this, that your IT security is sufficient to address these challenges, the following section might change your mind.
Unique IoT Device Characteristics
Traditional security approaches, which are more IT-centric, are not enough given the unique characteristics of IoT devices that make them vulnerable.
Scale & Accessibility
The sheer number of IoT devices, and the locations where they are deployed, make it extremely difficult for traditional security approaches to be as successful. For example, in some cases it may be challenging to reach all IoT devices due to connectivity issues. When the number of devices is in the hundreds and thousands, and if they are not in the same cellular network, the challenge to synchronize security patch management can be even more daunting.
Resources
Even if a customer can reliably get to all of their IoT devices, the limited computing power on these devices can make it impractical to run traditional security countermeasures like security agents or penetration tests. As such, continuous, on-device security maybe infeasible.
Device Lifetimes
The majority of IT network applications and endpoint devices are well defined in the corporate network and are regularly maintained. In contrast, IoT devices can be widely dispersed around the world and have very long lifetimes. In the event of an unforeseen vulnerability discovered after the IoT devices have left the factory, sometimes referred to as a “zero-day” attack, it is extremely difficult to patch the hardware or firmware long after they have been deployed.
Heterogeneity
IoT deployments may consist of many types of devices from different vendors. Rather than treating all devices the same way as a traditional IT security strategy is designed to do, it is safer to adopt a different approach where IoT networks are segmented from other networks. Even with a single type of IoT device, the hardware, firmware, and application may originate from different vendors, which makes identifying threats and vulnerabilities across all three very challenging.
IoT Network Security Requirements
Cellular networks have traditionally been considered a “black box” of little visibility by the manufacturers of the IoT devices and their customers. More often than not, they are left in the dark about their IoT network activity since they don’t have sufficient technical expertise. They might also lack a carrier relationship that helps them get the most from their IoT program.
Relying on a virtual private network (VPN) and access point name (APN) to improve IoT security is not enough. VPNs can protect data from being sniffed by unintended actors, but they do not prevent devices from talking to rogue/unauthorized endpoints; from “attacking” one another or legitimate endpoints; or from talking to another third-party endpoint. And while encryption of IoT communications is typically implemented at the application layer, network-based monitoring can verify that communications are actually happening over encrypted channels.
Like VPNs, APNs are a security control measure, and their role is to enable a carrier-specific connection to the internet, reducing the number of entry points to devices connecting on the network, but it does not provide protection beyond that. While using VPNs and APNs are standard practice for any IoT security program, they are not sufficient by themselves to protect IoT devices.
Augmenting IoT security with ML and AI at the cellular network level can further strengthen IoT solution providers’ existing IoT security programs by detecting rogue actors that VPNs and APNs are ill-equipped to prevent, especially at IoT scale. It’s this network intelligence that increases visibility into device behavior and reduces the level of human involvement needed to manage and secure IoT programs.
Built on the foundation of machine learning and artificial intelligence, the Aeris Intelligent IoT Network complements human intelligence to improve the speed of data processing and the detection of anomalies by processing data faster, baselining the characteristics of each deployment, and extracting actionable insights at the scale of IoT deployments.
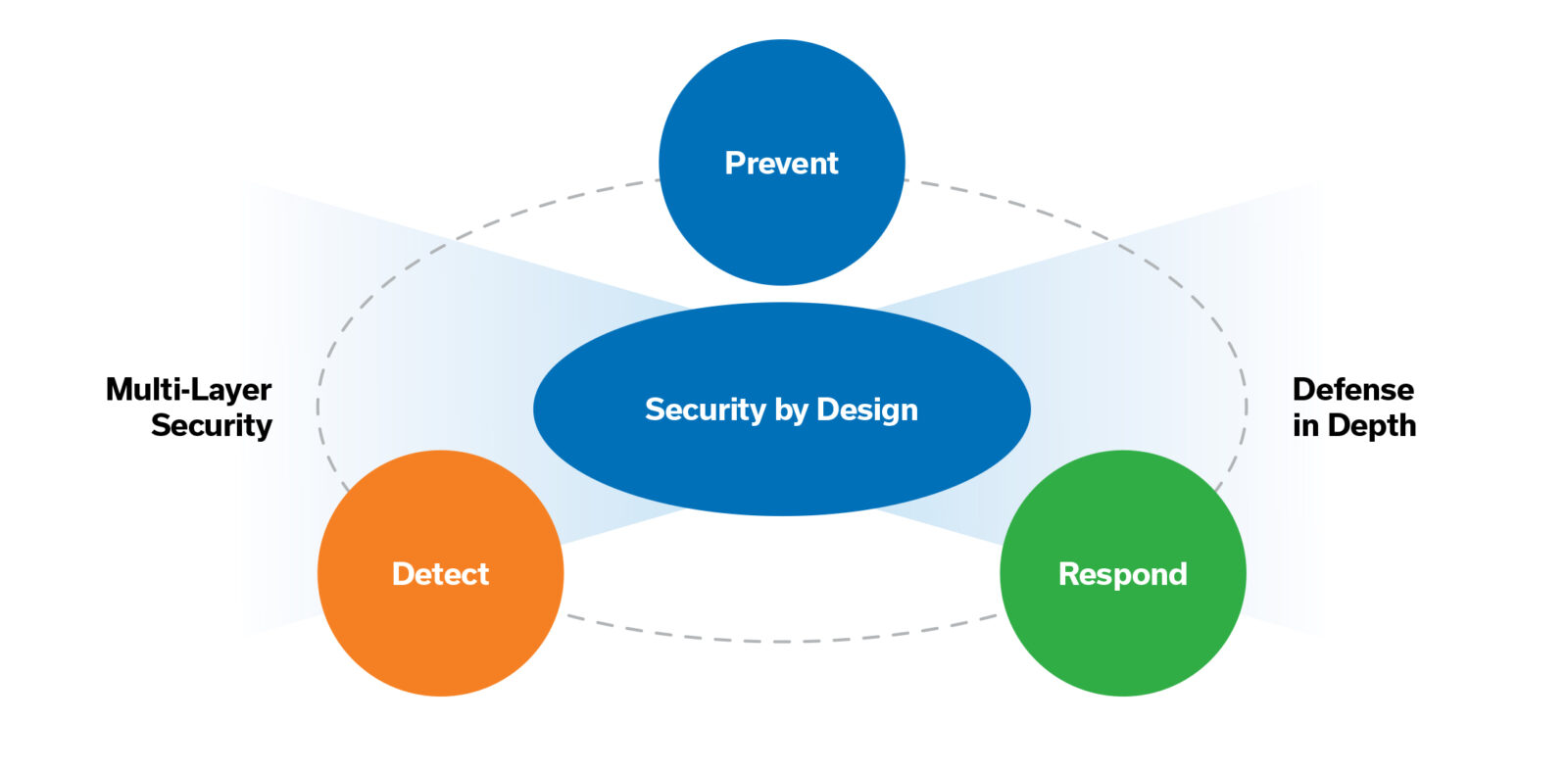
Adding this layer of security at the cellular network level can address gaps in security, reinforce IoT programs, and should be included as part of a secure-by-design, multi-layer security approach. This approach follows a robust architecture design at the onset of deployment and incorporates security measures at the device, application, data, and network level.
Security by design complements a defense-in-depth strategy in which multiple layers of security measures are used throughout the security architecture to provide redundancy.
Security by Design
Security by design is an approach to safeguard software and hardware and make them less vulnerable to abuse and/or security threats. This approach also needs to include applying security measures at the cellular network level. With Aeris, you can leverage the Aeris Intelligent Security Center (AISC), which uses network intelligence and machine learning technology to provide added cybersecurity capabilities that protect your cellular IoT devices. This latest innovation from Aeris is an agentless, network detection and response (NDR) capability and is part of the connectivity management platform of the Aeris Intelligent IoT Network. It provides seamless and near real-time detection and remediation, and there is nothing to install and nothing to configure. There are several unique advantages with AISC.
AISC provides continuous non-intrusive monitoring, behavioral analysis, and the ability to detect offline devices or rogue actors, and it enables visibility and analysis of security risks across multiple vectors – not only at the network level but also at the individual endpoint.
Analytics and machine learning also make it possible to leverage automation to trigger alerts, integrate with incident management systems, and expedite issue resolution. Advanced, deep forensic analysis improves the investigative workflow by seamlessly combining near real-time and historical data so that IoT solution providers can quickly identify and rapidly respond to potential security incidents within minutes, instead of months.
By extending your company’s security posture to your cellular IoT devices, you can quickly identify and take action against potential threats and rogue actors quickly. This will minimize service disruption, customer impact, and any lasting damage to your company’s reputation. With an agentless NDR security solution like AISC, you can easily, quickly, and cost-effectively prevent, detect, and respond to vulnerabilities and cybersecurity threats for your entire IoT program.
For more information about intelligent IoT network security and AISC, view our IoT security video.